Product Updates
Safelisting | Important Updates
We recommend implementing this update to ensure your security awareness program runs smoothly. Information about Safelisting can be found from the home page of the Community on the Safelisting tile, which you can access by clicking on “Community” in the top-right hand corner of the Security Education Platform.
Changes of Process for Microsoft Safelisting
This June Microsoft announced a change to how they safelist for content like phishing simulations. If you have Office 365 or Exchange Online we recommend following their guidance. We encourage customers to read the Microsoft article on safelisting and implement changes as soon as possible. These changes are being implemented by Microsoft over the coming weeks.
The safelisting domains are the same as what are currently published in the Community, but Microsoft has changed the location of where these items are safelisted in their product.
If you do not implement these changes there is the chance that:
-
Delivery of phishing simulations may be irregular
-
Certain templates will be impacted, while others are not
-
Some simulations may be quarantined by Microsoft
New Home Page and Content Browsing Experience
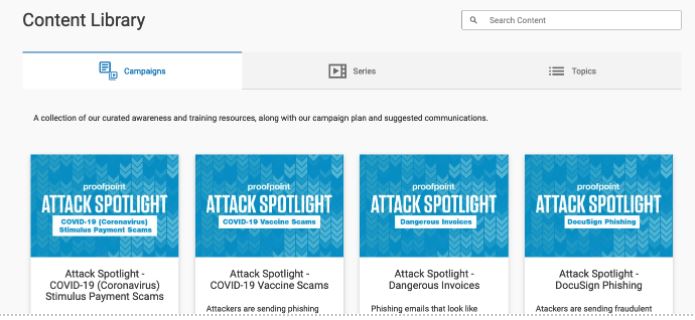
Finding the right content for your users has never been more important with the increase in people-centric attacks and your people working remotely. That’s why we’re excited to share a brand new way to find relevant content with our redesigned homepage.
By default you’ll see campaigns, which are curated awareness and training resources so you can run an impactful multi-channel campaign.
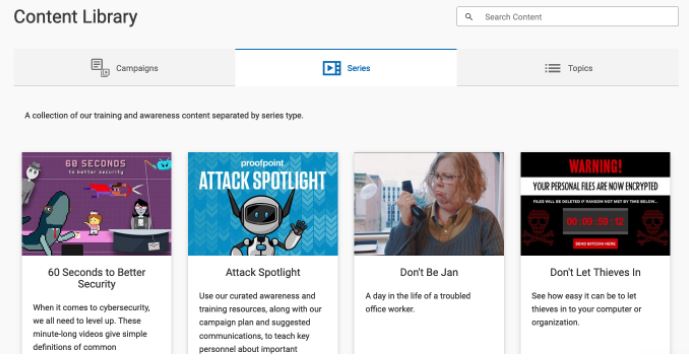
You can also view content by series, making it easier to provide a thematic experience for some of our much-loved content.
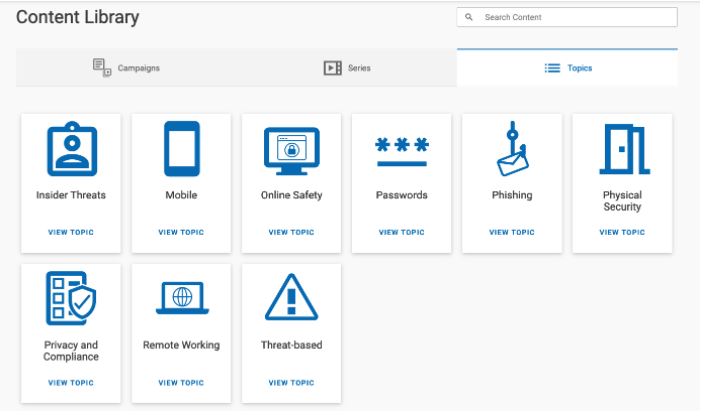
If you’d like to view specific content based on control domains or topics, our final tab will make it easy to do just that.
Clicking on any campaign, series or topic card on the browse page will automatically drill down to the Content Search results page of related content. Admins can continue to use search and filter on the Content Search page to further narrow the results to find the perfect match for their program needs.
Improved Reporting Functionality
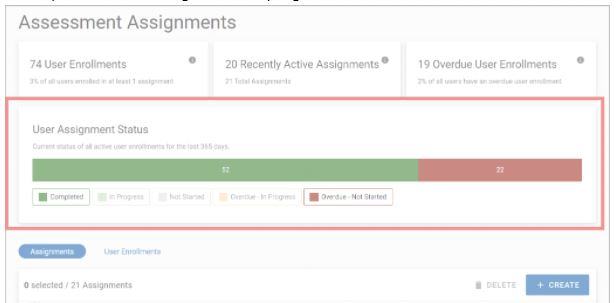
Our new real-time reports get you results, fast. So you can share with key stakeholders and keep them updated about assignments in progress.
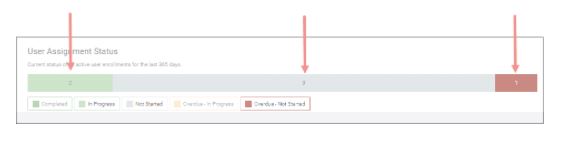
We’ve added a User Assignment Status bar to our Knowledge Assessment Assignments page, so you can see at-a-glance how your assessment is progressing. All status bars across our real-time reports will now display the number of users in each status.
Tell us what you think by clicking the feedback link on the training page.
Reporting Transition to Real-Time
We are in the process of moving from our previous report styles to our new real-time reports. You may see changes in the coming months, with reports being renamed and prior reports being replaced with the new format.
A few notes about these changes:
- Real-time reports will show two years worth of historical data which will be available for export
- Custom properties will be available from legacy reports and in the future can be exported, self-service from the platform
- Scheduled exports will continue from the legacy reports
- New Real-time reports will supplement legacy reports, so customers can access both for the time being
Our teams are working hard on transitioning to our enhanced real-time reports with similar functionality and features you’ve come to expect from legacy reporting.
Content Updates
We numerous new assets for you to consider for this month. (13) new assets include an “Attack Spotlight: ICS: An Introduction”, (9) new interactive training assets covering global privacy regulations, vishing, healthcare, and vendor management. Plus, (3) new interactive awareness modules on HIPAA, whaling and ICA. Finally, we have (7) assets with translation and diversity updates:
Interactive Awareness Modules:
- “Australia's Privacy Act” –This awareness video provides a detailed review of the Australia Privacy Act. Topics covered include applicability, how sensitive information is defined and a review of Australian Privacy Principles. In addition, it reviews topics of consent, responsibilities, breach notification, international data transfers and how it differs from GDPR.
- “Brazil GLPD” – The awareness asset provides users details on LGPD, including how sensitive and anonymized data is defined, lawful processing, individual rights, consent, and the responsibilities of organizations. Finally, LGPD is contrasted to GDPR.
- “Customer Service: Vishing” – Customer service staff are prime targets of phone and voice mail phishing, or Vishing. This role focused asset guides customer service staff to recognize and avoid vishing attacks.
- "Healthcare: Online Social Media” – Healthcare workers must be extremely cautious with their online activity to prevent accidental sharing of confidential or patient information. This asset provides guidance on how to share on social media without creating risk for their organization.
- "Hong Kong's Personal Data Privacy Ordinance" – As Asia’s longest standing privacy regulation, it is important for organizations to understand its data protection principles. Users will be introduced to Hong Kong's Personal Data Privacy Ordinance (PDPO) and its proposed changes.
- "Privacy Regulation in China” – This awareness video provides a review of the complex privacy landscape in China. It reviews the principles about personal data collection and use that are encompassed in the Cybersecurity Law and the Civil Code, and the guidance provided by the Personal Information Security Specification.
- "Singapore's Personal Data Protection Act” – Singapore has established leadership in privacy law, both in definition and enforcement. Users will learn about Singapore's Personal Data Protection Act (PDPA) and review its newest amendments from 2020.
- "South Korea's PIPA" – South Korea’s comprehensive Personal Information Protection Act was enacted Sept. 30, 2011. It is one of the world’s strictest privacy regimes. Users will learn about South Korea's Personal Information Protection Act (PIPA) and its differences from the General Data Protection Regulation (GDPR).
- "Vendor Management: Sharing Data with Third Parties" – Sharing data with third parties can be very risky. This awareness video reviews the best practices for sharing information with third parties to minimize risk.
Training Video:
- "Attack Spotlight: Amazon Phishing Scams" – With the popularity of Amazon, it has become a frequently used scam to entice users into actions that will compromise their confidential information, that can lead to fraud or personal data loss. Users will learn how to recognize and avoid Amazon Phishing scams.
Interactive Training Modules:
- "Spot the Risks: HIPAA Privacy & Security Game" - Scammers are using Google Drive to send out legitimate-looking email and mobile notifications that invite recipients to view, download, or collaborate on files. The Attack Spotlight campaign on Google Drive phishing will help educate your users on how to spot and avoid these deceptions.
- "Whaling Threats"- Users could be targeted in a whaling attack because of their role, visibility, and access privileges in your organization. In this module, they’ll learn how to recognize the techniques used in these attacks, and how to implement safeguards to mitigate the impact of whaling.
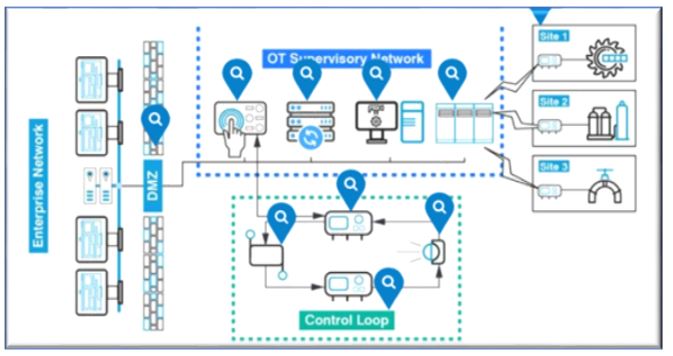
- "The Anatomy of ICS Environments" - Users will receive an overview of the technology, processes, and people commonly found in industrial control systems (ICS) environments.
Updated/Revised Content:
7 Training and Awareness Video Updates
- "ICS: An Introduction" - now in 12 languages
- Update to 5 "Security Tonight" videos - now in 6 languages
- Business Email Compromise
- Insider Threats
- Phishing
- Physical Security
- Ransomware
- "Prison Break......In?" - diversity update